3-2-1 Backup Evolution: Modern Strategies for Data Protection
In the realm of data protection, the 3-2-1 backup strategy has long been a cornerstone, guiding individuals and ...
In the realm of data protection, the 3-2-1 backup strategy has long been a cornerstone, guiding individuals and organizations in safeguarding their critical data. However, as technology evolves, so do the challenges and solutions in data backup and recovery. Let's explore how this strategy has adapted over time and the modern alternatives that are shaping the future of data protection.
Understanding the 3-2-1 Rule
The 3-2-1 backup strategy is straightforward: keep three copies of your data, store them on two different types of media, and keep one copy offsite. This approach has been widely endorsed due to its simplicity and effectiveness. However, as we delve into the digital age, the limitations of this rule have become more apparent.
In all these strategies, the idea is to keep your important things (like data) safe in different ways and places, so you don't lose them if something unexpected happens. Just like you protect your toys, recipes, or photos, these strategies protect important computer data.
Criticisms of the 3-2-1 Rule
Originally designed to protect against physical threats like disk failures and natural disasters, the 3-2-1 rule doesn't fully address today's cyber threats, such as ransomware. Critics argue that the rule, while still valuable, may not be the most optimal solution for all scenarios, especially considering the cost and complexity of maintaining multiple data copies.
The Shift in Threat Landscape
In our current digital era, cyber threats pose a significant risk that the traditional 3-2-1 rule may not adequately address. The increasing size of data sets and the cost of maintaining multiple copies have also raised questions about the feasibility of this strategy.
Modern Alternatives to the 3-2-1 Rule
In response to these challenges, alternative strategies like the 3-1-2, 3-2-2, and 3-2-3 have emerged. These variations place greater emphasis on offsite and cloud storage, offering enhanced protection against both physical and cyber threats.
-
3-1-2 Strategy
Imagine you have a precious family recipe. To keep it safe, you make three copies of it. You keep two copies at home in different places – maybe one in your recipe book and another in a kitchen drawer. The third copy you give to your grandma to keep at her house. This way, if something happens to your copies at home (like a kitchen mishap), you still have the recipe safe with grandma. In the 3-1-2 strategy, the '1' means one type of storage (like paper for your recipe), and the '2' means two places (your home and grandma's house).
-
3-2-2 Strategy
Now, let's say you have three favorite toys. To make sure you don't lose them, you keep one at home, one at your best friend's house, and one at your cousin's house. That's like having three copies of your data. But here's the twist: you put each toy in a different type of box – one in a wooden box, another in a plastic container, and the third in a metal tin. This is like storing your data on two types of media (the different boxes). Lastly, you keep two of these toys (in their boxes) outside your home – at your friend's and cousin's. That's the '2' in 3-2-2, meaning two places outside your home.
-
3-2-3 Strategy
Think of it like having three special photos. You print these photos on different materials – one on paper, another on canvas, and the third as a digital photo frame. That's your three copies on two types of media. Now, you keep these photos in three different places: one at home, one at your uncle's place, and the last one at your school locker. So, all three copies are in different locations, ensuring that if something happens at one place, the other photos are still safe.
Myota's Innovative Approach
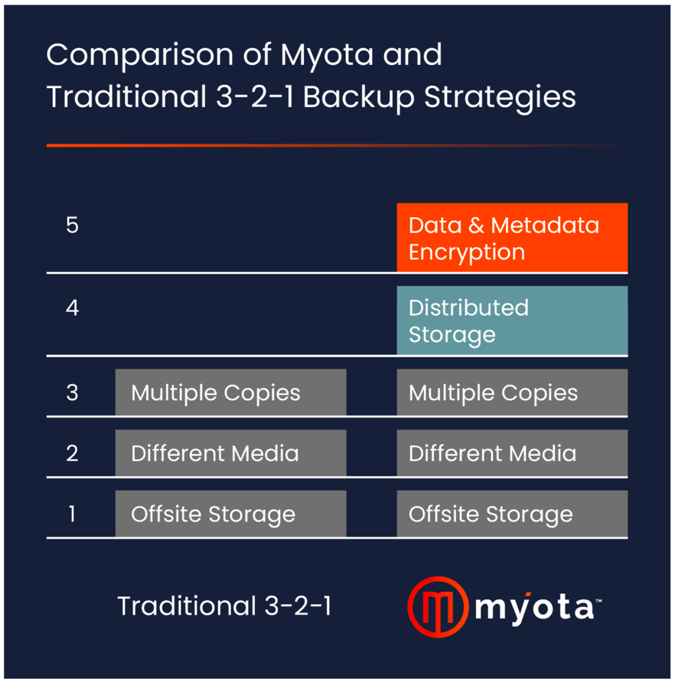
Myota has developed a patented method for data protection that can adapt to these modern strategies. The Shred and Spread™ method integrates quantum-proof encryption with flexible data storage strategies. This approach involves encrypting data into immutable shards and distributing them across different storage nodes, ensuring data durability and security.
Cost-Effective Implementations
Myota's approach to the 3-1-2, 3-2-2, and 3-2-3 strategies is not only flexible but also cost-effective. By distributing encrypted data across multiple nodes, Myota ensures data is not only backed up but also safeguarded against unauthorized access, all while reducing CapEx and OpEx.
Exceeding Cyber Insurance Thresholds
Myota's commitment to robust data backup strategies goes beyond traditional methods. By continuously monitoring and updating its strategies, Myota aligns with the evolving landscape of cyber threats and technological advancements, exceeding the thresholds set by cyber insurance policies.
Conclusion
The evolution of the 3-2-1 backup strategy reflects the need for flexibility and improved protection in our ever-changing digital world. With innovative solutions like Myota's Shred and Spread™ method, businesses can adapt their backup strategies to meet modern challenges, ensuring their data remains secure and accessible in any scenario.

